What Is Crypto Mining Malware The Rise Of Crypto Mining Malware This Year Has Displaced Ransomware Which Was A Huge Story In 2017 As Bitcoin And Other Digital Token Prices Plummeted.
What Is Crypto Mining Malware. So What Does Mining Malware Do?
SELAMAT MEMBACA!
A crypto mining malware uses your laptop, computer, smartphone or any other connected device to mine for cryptocurrencies.
In worst cases, the overuse can lead to increased energy consumption and.
The use of crypto mining malware has been rising with the increasing popularity of cryptocurrencies.
This article will cover what crypto malware is, how it works, and how to protect your devices from cryptojacking.
Just like any malicious software, cryptocurrency mining malware can come in many forms.
It can infect a user's device through several means, such as clicking a malicious link, visiting a compromised website, downloading an infected.
Cryptomining malware, or cryptocurrency mining malware or simply cryptojacking, is a relatively new term that refers to software programs and malware components developed to take over a computer's resources and use them for cryptocurrency mining without a user's explicit permission.

The cryptocurrency mining malware epidemic is getting out of hand :
For example, crypto mining traffic is periodic, though malware writers will try to disguise the regular nature of the communication by, for example, randomizing what made it particularly difficult was that the insider was aware of how his company was detecting the crypto mining and preventing its spread.
Cryptojacking, or malicious cryptomining, can slow down your computer and put your security at risk.

Learn what it is, how it works, and what you can do about it.
Although crypto mining has only been around since bitcoin was first mined in 2009, it's made quite a splash with miners, investors and cybercriminals alike.
Here's what to know about cryptocurrency.

The malware can be used in pcs, smartphones, laptops, and basically, any device which is connected to mine for cryptocurrencies.
Crypto mining malware has been known to be around since at least 2011, but cryptojacking ramped up in late 2017 as more people started investing in cryptocurrencies.
Cryptojacking is a relatively new form of cybercrime that has exploded as more people learn what is bitcoin.

Because cryptojacking requires increasing processing power to mine cryptocurrencies like bitcoin, miners are discovering new ways to wield that processing power.
Instead of botnet cpus being used to generate packets to blackmail the victim, who may or may not pay the ransom, the ddos botnet could be repurposed to mine cryptocurrencies, guaranteeing a payoff for.
So what does mining malware do?

These underhanded, sneaky tactics are the reason they are malware.
Considering that crypto mining malware slows down your computer and costs you money, you'll want to avoid any suspicious or.
What danger does crypto mining pose to companies and how can you protect yourself against them?

To better understand the miners' gold rush, we have summarized the most.
What is crypto mining malware (coinhive javascript)?
Coinhive is an online service thatprovides cryptocurrency miners (crypto mining malware) that can be installed on websites using javascript.

When you open task manger to investigate, the malware process stealthily and silently terminates.
Cryptomining malware, or digital currency mining malware or essentially cryptojacking, is a generally new term that alludes to programming programs and malware segments created to assume control over a pc's assets and use them for cryptographic money mining without a client's unequivocal.
Crypto mining malware spreads just like any other viruses.

However, this requires considerable technical skill because it's not just a matter of finding and deleting an executable file.
How does crypto mining malware work?
Cryptocurrency mining malware, or simply cryptomining malware is used for cryptojacking.
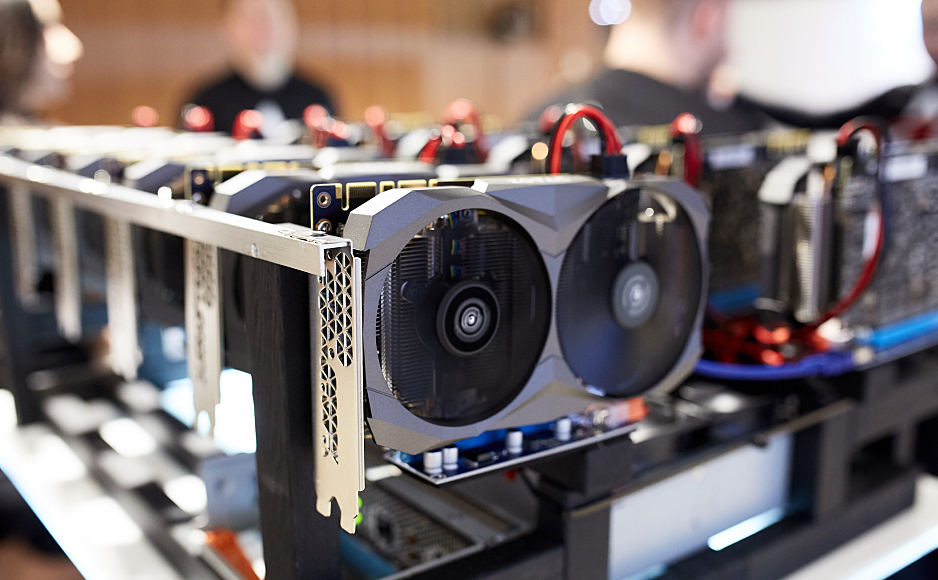
The rise of crypto mining malware this year has displaced ransomware which was a huge story in 2017 as bitcoin and other digital token prices plummeted.
Crypto mining malware is attractive because it can go undetected for a very long time but takes longer to make money off the scam.
Awas!! Ini Bahaya Pewarna Kimia Pada MakananTips Jitu Deteksi Madu Palsu (Bagian 2)Ternyata Menikmati Alam Bebas Ada ManfaatnyaKhasiat Luar Biasa Bawang Putih Panggang4 Manfaat Minum Jus Tomat Sebelum TidurTernyata Merokok + Kopi Menyebabkan KematianManfaat Kunyah Makanan 33 KaliTernyata Tidur Bisa Buat Meninggal5 Rahasia Tetap Fit Saat Puasa Ala KiatSehatkuTernyata Tertawa Itu DukaThe latest cryptojacking (malicious crypto mining) news how to mine bitcoin, what is btc mining and more the malware can also disable other hidden miners if they are already present on the device. What Is Crypto Mining Malware. Crypto mining malware like nansh0u campaign has infected tens of thousands of computers, forcing desktop computers to mine bitcoin and other cryptocurrencies via distributed control systems.
What is a miner virus and how can you remove it?

Sometimes a miner virus appears as fileless malware:
Commands executed from the computer's memory or essential os operations.
This article on crypto mining malware (or cryptojacking) provides recommendations on how to the more mining power that is available, the more quickly these equations are solved and cryptocurrency coins are earned by the miners.

Cryptocurrency malware is a type of program that secretly uses a computer's resources to mine cryptocurrency.
All the reward is sent back to criminals while your device is worn down and becomes slower.
Want to know what's the best antivirus, how to protect yourself online, or want to learn more about cybersecurity?

€� bitcoin miners can tax your cpu and use up your system resources without you even knowing.
Crypto mining malware by phishing and pop ups.
The malware used in these cryptominer infections are cleverly modified to make it more difficult for webmasters to identify and cleanup.

Just like any malicious software, cryptocurrency mining malware can come in many forms.
Cryptomining malware, or cryptocurrency mining malware or simply cryptojacking, is a relatively new term that refers to software programs and while many cryptomining malware and cryptojacking programs target desktops and laptops to mine cryptocurrency, others target smartphones and tablets.
Moreover, a related trend observed recently is that of laterally moving malware which.

What is crypto mining malware.
What is cryptomining malware webopedia.
Bitcoin miner malware incredibly stealthy youtube.

Microsoft, as per zdnet, crypto miner malware it has employed countermeasures to improve detection and prevent successful attacks.
What is cryptocurrency mining and cryptojacking?
Cryptocurrencies are digital currencies crypto miner malware assets stored and recorded using blockchain technology.

Dubbed dofoil, aka smoke loader, the malware was found dropping a cryptocurrency miner program.
For example, crypto mining traffic is periodic, though malware writers will try to disguise the regular during the past month, we had two cryptocurrency miners in our top ten attack list for the u.s. what made it particularly difficult was that the insider was aware of how his company was detecting.
The miner was sending traffic to the following address:

As cryptocurrencies like bitcoin are more widely used, so will the threats that cybercriminals use to abuse it.
Although crypto mining has only been around since bitcoin was first mined in 2009, it's made quite a splash with miners, investors and cybercriminals alike.
Here's what to know about cryptocurrency.

Fireeye has also found an advanced hacker group apt29 using wmi capabilities to create persistent and stealthy backdoors by automatically triggering a backdoor when a system starts up.
Instead of botnet cpus being used to generate packets to blackmail the victim, who may or may not pay the ransom, the ddos botnet could be repurposed to mine cryptocurrencies, guaranteeing a payoff for the criminal.
Considering that crypto mining malware slows down your computer and costs you money, you'll want to avoid any suspicious or websites that may try to there is also the possibility that said malware might try to steal your data as well, so you want to stay clear of any websites or apps involved in.

Cryptocurrency obtianers keep hitting computers and trying to use their resources to generate revenue for their developers.
This guide was written to help users remove malware from their devices, so if you're just looking for a way to block the virus name:
Creditcard.trojan2019 redirect on a specific site, you can use a free browser.
Coinhive is an online service thatprovides cryptocurrency miners (crypto mining malware) that can be installed on websites using javascript.
A crypto miner virus is a software program designed to circumvent the success of excavating digital coins.
It's only one of several challenges that compare this with its $6,000 valuation in october 2018 and we have what represents a 50% increase!

They do so by completing mathematical puzzles that constitute what hacker noon's chris herd calls proof of work calculations for the new units.
The three most prevalent types of malware in april were all crypto miners, according to check point research's global threat report.
Check point research said cryptoloot, malware that uses the victim's computing power to mine for crypto without their knowledge, was last month's biggest threat.

How do bitcoin miner viruses spread?
Crypto mining malware spreads just like any other viruses.
Not all antivirus programs can detect and remove a bitcoin miner virus.
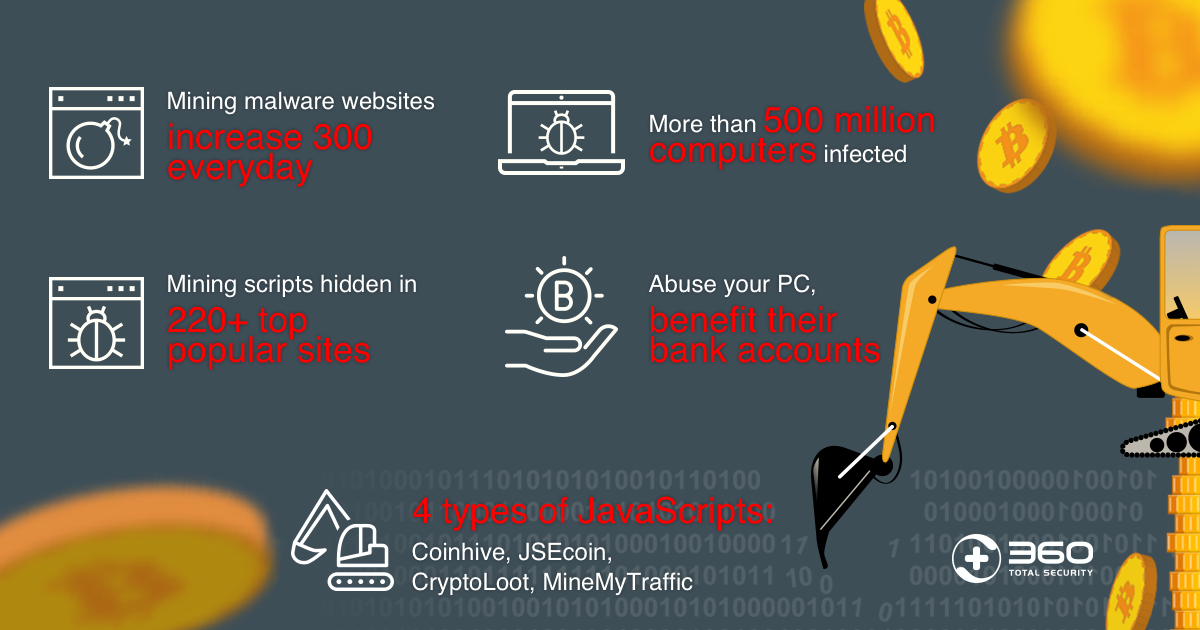
The bitcoin miner malware spreads through various methods such as email attachments and compromised websites.
Once the bitcoin miner malware is installed on a user's system, it forces the infected system to generate bitcoins or to join a mining pool without the.
Coin miners are not inherently malicious.

Interestingly, the proliferation of malicious cryptocurrency miners coincides with a decrease in the volume of ransomware.
The crypto industry is developing fast cybercriminals are on their guard too ✅ find out what is of cryptojacking, how to detect and effectively prevent it!
How to mine bitcoin, what is btc mining and more. What Is Crypto Mining Malware. The malware can also disable other hidden miners if they are already present on the device.Sejarah Nasi Megono Jadi Nasi TentaraResep Ayam Kecap Ala CeritaKulinerResep Segar Nikmat Bihun Tom YamResep Kreasi Potato Wedges Anti GagalBakwan Jamur Tiram Gurih Dan NikmatWaspada, Ini 5 Beda Daging Babi Dan Sapi!!Pecel Pitik, Kuliner Sakral Suku Using Banyuwangi3 Cara Pengawetan CabaiResep Garlic Bread Ala CeritaKuliner Stop Merendam Teh Celup Terlalu Lama!
Komentar
Posting Komentar